UBLockdown 2024
UBLockdown v16
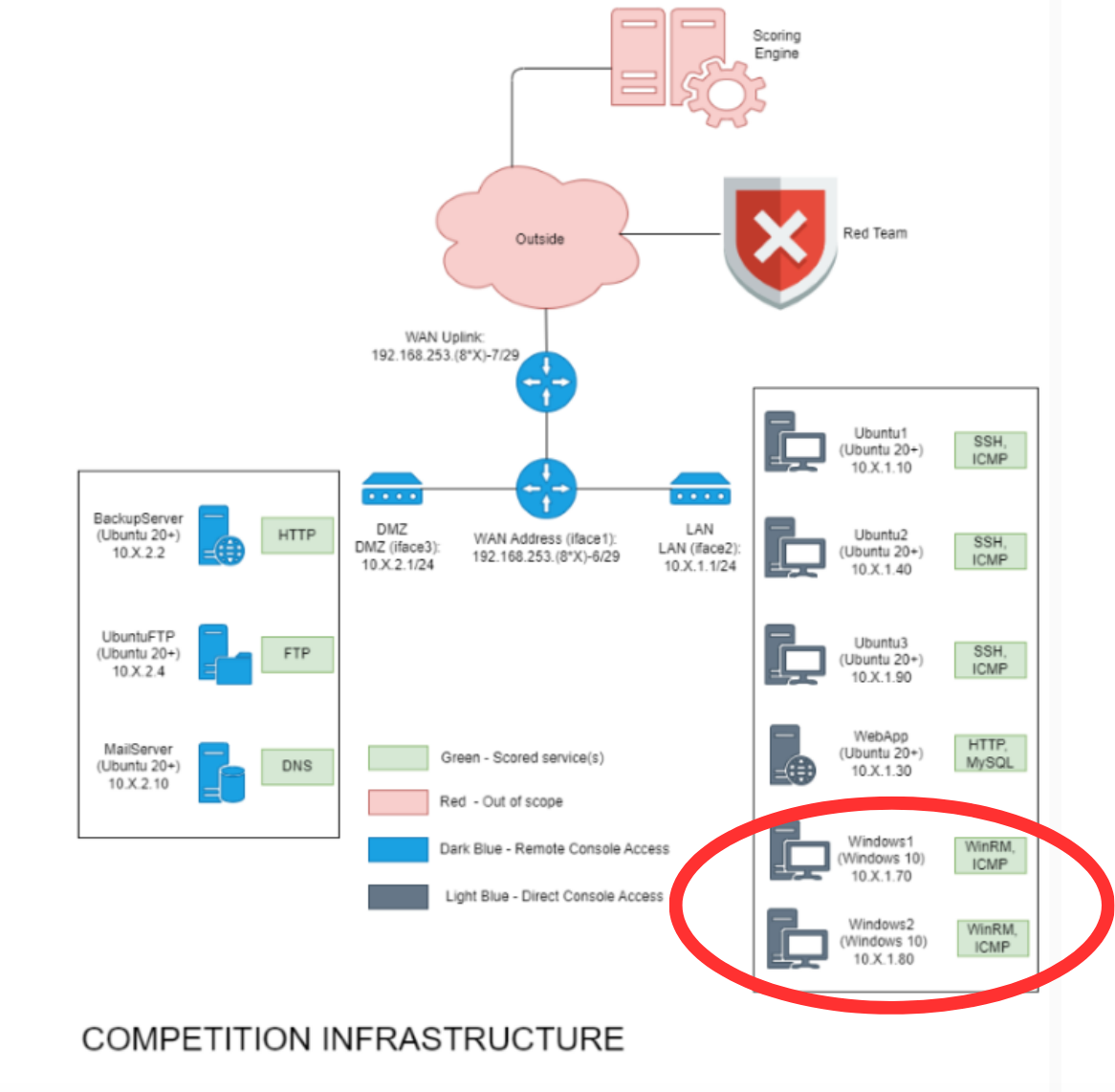
Competition Topology:
This competition was a blue team-only competition that featured a wide variety of machines, with an array of operating systems to work with. The operating system I was tasked with for my first competition was Windows 10, as highlighted. The overall network topology was quite complex providing a spectrum of services ranging from MySQL to FTP. My task seemed simple: to keep WinRM and ICMP online.
My Strategy:
With the help of my amazing team, I was capable of devising a well-thought-out strategy, or what I thought was a well-thought-out strategy (we will touch on this later). My first step was simple: change the password to the admin user which I was already logged into. I mean with a password like Change.Me! you cannot expect to be extremely defensive against those pesky Red Teamers. My passwords of choice were tHeDucky45! and tHeDucky46!, seems pretty strong right? After changing the passwords, I saw a plethora of unique usernames such as IceSpice, Fortnite, Call of Duty, and many more (interesting twist Ubuffalo, gave me a good laugh). I decided having 30 users with admin access to both of my machines wouldn’t be the best idea, so I took all of those users away as I was not being scored on a single one. Next, I made it to the sweet Sysinternals suite, no pun intended. I ran AutoRuns64 which allowed me to see the scope of malware and nonsense put onto my systems before I even touched them. It ranged from Powershell scripts named “Malware.ps1’’ to Batch files “secret_malware.bat” to what would be considered normal Windows software like TacticalRMM, which was of course used maliciously. They also implemented multiple Cron jobs to capture my actions, so I got rid of those as quickly as I could. After removing all of the malware, at least that’s what I believed, I wanted to begin hardening my systems.
My Attempt At System Hardening/Threat Hunting:
My first attempt at threat hunting was using an open-source software called winPEAS, this would allow me to seek out potential avenues for privilege escalation in my systems. However, as a first-time user of both Powershell and winPEAS, my lack of knowledge left me hopeless on how to use this information to defend my systems. After countless Google searches, I began to understand some of what I saw, but by then it was too late. This gave me a great opportunity to learn what open-source software is available, and I look forward to my next chance to use winPEAS successfully. My first thought when it came to system hardening was using the Windows Defender Firewall; however, our team had already planned to use a pfSense firewall configuration on the router, so I was advised to not configure this in my systems. Since this was my first time ever working to defend and protect a Windows system, the ideas for threat hunting and hardening were slim to none. In order to improve my skill set, I plan to work hard in this department to ensure I can provide more value to my team.
Results:
By the end of the competition, everyone’s services were completely wiped out from head-to-toe. I was proud of the efforts I made, and it was enough to leave my WinRM and ICMP up on both machines until around the final hour. I tried to reconfigure my WinRM using a multitude of command-line options, but it was to no avail as the Red Team had already completely messed with my default configuration. You may be wondering, well where was your backup configuration copy of the default WinRM config. Ah, I began to wonder the same thing. Rookie mistake. My WinRM was unrecoverable; but my machines continued pinging until the Red Team completely shut down our router, demolishing our entire network. Our team placed 10th out of 15 teams, missing one teammate and having three as first-time competitors. I am proud of what our team accomplished and look forward to working with Aiden, CJ, Daniel, and Rohan in the near future.
Red Team Review:
This is where things get ugly. So let’s go back to this line, “After removing all of the malware, at least that’s what I believed, I wanted to begin hardening my systems.”, oh how wrong this thought was. After the Red Team displayed all the tactics they used, I was shocked my system was not decimated sooner. The moment I changed my initial password, I figured my password was safe, they were logging the new password through a Run/RunOnce registry Key. This meant that all of the malware I got rid of and cron jobs I stopped was practically useless as my systems were open to them 24/7. In order to combat this, I plan to change the passwords of my systems multiple times. Initially at startup it is a necessity; however, in wake of this technique, I will be changing passwords after removing malicious techniques. Another threat vector was process injection, which I could have used other items in the Sysinternals suite such as Process Explorer, to seek out the malicious processes which in this case were DLLs. The one threat vector I did completely mitigate was the Startup folder created by the Red Team, which as stated earlier I noticed while reviewing Autoruns. Overall, the Red Team completely destroyed everyone and had fun while doing it so props to them.
Final Thoughts:
As a first-time competitor, I had a lot of fun working with my team and learned a ton while doing it. We had a great group with multiple skill sets that allowed us to keep a majority of the network alive until the final few hours. I look forward to continuing learning and making myself a better cyber defender and competitor. I want to thank UBuffalo for hosting a wonderful competition for all of us to learn from, it was a blast. I am eager to compete more often and this was extremely fun to not only write about but discuss with my peers.